An Introduction to CrossConnect & The Three Concerns
I am not entirely sure how I arrived at this point. After fifteen years of working in tech I was tired of building for others and wanted to focus on my own projects. I resigned from my position just in time to miss the Great Work-From-Homenning of 2020 and began consulting. I was able to put my expertise in systems architecture to good use when my children suddenly required technical deep dives for Zoom and Teams. Their skill in the domain of remote learning software, however, soon exceeded my own and I found myself free to experiment and develop the perfect recipe for chocolate chip cookies. In between establishing a strategic reserve of baking supplies and fulfilling my duties as in-house teacher’s aid, I began to think about the issues facing the industry in which I had toiled for the better part of my adult life.
Telecommunications was becoming progressively consolidated and centralized. Increasingly reliant on revenue driven by data delivery, the world’s mobile Communication Service Providers, or CSPs, appeared to be misnamed. A more apt description for modern times might be Wireless Internet Service Providers, as the communication services we use rely on a handful of large tech companies. Our interactions now depend on a select few enterprises, including Google, Apple, Microsoft, Facebook, Amazon, and Tencent.
From a structural perspective, and despite their flaws, a human communication ecosystem composed of a thousand telecommunication providers is preferable to one built by fewer than ten tech giants. The centralization of interaction in the form of these near-monopolies has produced an enormous benefit to end users in terms of utility, but as we place more power into fewer hands, the potential for abuse and corruption increases. If banking, browsing, texting, teleconferencing, voice, video, and all other forms of digital interaction were unified under a single provider for all the people of Earth, we would achieve untold levels of user experience nirvana. But if choice is the heart of freedom, then this would be the death of liberty.
Ecosystems
I asked myself how we could improve both the incumbent legacy system and our new digital communications reality. I felt that the core issue of centralization plaguing my specific industry segment, mobile messaging, was caused by the overwhelming desire to capture users inside closed ecosystems, as they represented potential revenue through data extraction and market control.
These business practices are typically exploitative. Users who trade their data for the utility of a service are not truly able to consent to an exchange as they have no way of knowing the value of what they are exchanging. Moreover, in a closed ecosystem, the market is fully controlled by the provider who can engage in anti-competitive behavior. Businesses who wish to reach the captured audience must pay the price of admission for access.
The interests of the service provider are well represented in a closed ecosystem, but the interests of users and other commercial participants are subservient, common interest extends only as far as the economic interests of those in control. To better represent the common interest of all, what is needed is a fair and competitive playing field, as opposed to distinct monopolies.
Giving users more control through interoperability, portability, and the option for direct peer-to-peer user interaction could help produce such a result. Moreover, competitors should be free to innovate and create new functionality to attract users and generate revenue through explicit economic exchanges. These exchanges should be free from unjustified interference from those in control of the ecosystem. Some here would argue that we should rely on regulation and coercion from an outside entity, but these entities are also subject to self-interest and manipulation. Who then should make the rules, and how should they be determined?
If we are to decentralize control of the system to provide all stakeholders with a voice, we will require a different structure for our ecosystem in order to better represent the common interest. The traditional economic models of data monetization simply do not work if users are granted inherent rights, such as the right of portability and interoperability. A better representation of the common interest would require a common core infrastructure whose operation can balance the interests of participants.
Decentralized control of the common infrastructure is needed to enable a fair playing field for the ecosystem, the operation of our core systems must be neutral and must not unfairly advantage special interests. If the core infrastructure of our ecosystem is operated by a neutral third party, then instead of needing to federate or fully distribute functionality, which typically results in reduced innovation, adoption, and performance, we could instead centralize it and gain the advantages that this entails.
A new design will be required if we are to have thousands of CSPs, and other new potential providers act as one, and assist in the construction of an ecosystem that can compete with and outmaneuver the walled gardens of the tech titans. The self-interest of participants must be aligned into a common interest so that all may push in the same direction. If this is to be the path towards progress, then two major avenues require investigation. What should we build from a technical perspective, and how do we guarantee the neutral operation, or governance of what we have built?
Technical Overview
With an eye towards neutrality, interoperability, and decentralization I began architecting a system that would enable reachability based on the lookup of unique identifiers for participants. This seemed like a logical approach, as it was the absolute minimum functionality needed to enable forms of interaction, including telecommunication services such as messaging.
Users would be guided through a registration process which would prove their ownership of an identifier. This identifier could then be hashed and recorded on a private permissioned blockchain, or other datastore. Records would contain a hashed identifier, public key, and reachability server. The reachability server maintains contact with the user and the user indicates their preferred reachability server during the registration process.
By querying the record using an identifier, a sender can determine the reachability server of a receiver and initiate a connection request to the reachability server. Because the identifiers would be hashed, any sender attempting to lookup the reachability server for a given receiver must already know what the valid identifier is so that it may be hashed prior to the lookup request. The private/public key pair could be used to authenticate senders and receivers as valid participants in the network.
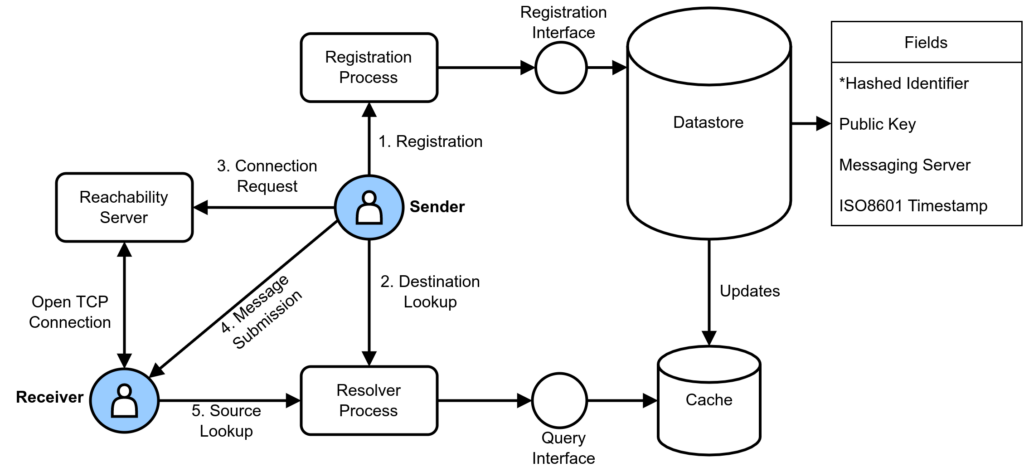
In theory this allows two separate closed messaging ecosystems to establish interoperability. As long as the receiver identifier is known, and the distinct communication services for sender and receiver agree on a method of data transfer, interoperability is possible, as our service assists in the formation of the initial connection by providing reachability information to the requesting sender.
The types of interactions and the ways in which they would be negotiated are determined by sender and receiver applications, as our core infrastructure would not concern itself with higher level complexity. Moreover, this design enables direct peer-to-peer exchanges as well as inter-server or server-client communication. These communications could take the form of text messages, voice, or video calls.
The proposed system represented the minimum viable centralization of function needed to enable a global communications ecosystem. By structuring our ecosystem in this way, instead of a series of walled gardens where entry is enforced by separate passports, users are citizens in an archipelago that can be navigated via routes that application creators have voluntarily chosen to establish.
Governance Considerations
The second item requiring investigation are the guarantees of neutrality in the operation, or governance, of the system. I searched for governance frameworks but could not find an example for exactly what I needed. Neutral governance for digital systems of economic exchange is a mouthful and yields few direct search results. It looked as though this required the creation of something new, something that didn’t exist, and as far as I could tell, a paradigm shift in our thought about how digital systems should function.
I could see the borders of what needed to be defined and traced a rough outline. Our ecosystem has three prevailing groups, users who were interested in the utility of the system, providers and people who were interested in profit, and a third group, a neutral construct concerned with aligning and balancing the interests of all participants. The basic structure, and the idea of a Neutral Concern, was not so much created as it emerged on its own. To me, the structure coalesced independently and came into existence as a logical conclusion once interests of all participants in a digital system were represented.
As I looked at the relationships between participants, this task which at first seemed a minor and straightforward consideration, proved to be extremely challenging. What mechanisms effectively decentralized control of the system? Who should have control and in what proportions? How do you guard against corruption? If the core functionality of the system is centralized, is that not inherently prone to abuse? How do you meaningfully demonstrate neutrality and trustworthiness? More importantly, how do we practically implement these considerations? I sketched and described what I could and continued with what I now understood to be the easier and less muddled part of the project, the technical design of the system.
Imitation As Flattery
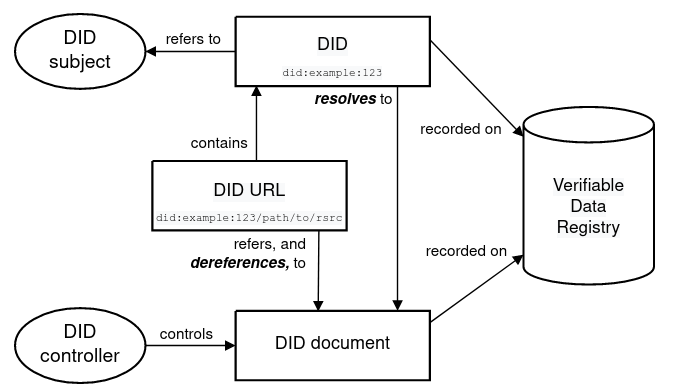
I named the project CrossConnect and in May of 2021 began work on defining the interfaces and mechanisms needed to build a proof of concept. I very quickly discovered that the majority of what I was proposing, and the work necessary to accomplish it, was already well underway. I had heard the name Self-Sovereign Identity (SSI) as I was interested in blockchain technology. When I began to examine Decentralized Identifiers (DIDs) and Verified Credentials (VCs) more closely, however, I realized that others had reached similar design conclusions.
SSI, or Decentralized Identity, is the concept of the inherent right to ownership of identity and its associated data. As opposed to users being dependent on centralized identity platforms, such as Facebook or Google, users own their identity. While my project concerning telecommunications was similar, the far more skilled and thoughtful people in the SSI ecosystem had created standards and technologies which could be applied much more broadly, as they proposed to alter the fundamental nature of identity on the Internet.
Decentralized Identifiers provide a way for identifiers to be resolved to a DID Document. This DID Document contains a Service Endpoint, public key, and other information. The service endpoint can be contacted to form connections with the subject (or receiver) in question. Sound familiar? For me, this provided some form of independent confirmation that I was on the right track.
In attempting to address an issue of consolidation and centralization in a telecommunications marketplace, I had unwittingly proposed a similar solution to the one which has been proposed to address existing centralized identity issues on the internet. My solution was far more limited, and not nearly as well thought out as what had already been proposed and built, but it had the same shape. I also discovered something far more puzzling.
Repeating Patterns
Governance had also been identified as a major consideration in the SSI ecosystem. Moreover, it was widely recognized as a challenge, governance is hard. By giving users the inherent right of identity ownership and data control, old models of economic exchange no longer functioned as they do not adequately represent the interests of users who now have leverage in an exchange. New conventions for interactions and marketplaces where exchanges take place must be constructed.
The structures present in these ecosystems require rules and mechanisms that can encourage or enforce the common interest while remaining commercially viable. I was struck by the fact that while working mostly in a vacuum I had somehow traced an outline similar to the governance structures being proposed for the new identity ecosystem. It appeared that granting inherent rights to users in a digital system produced similar structures regardless of the specifics of the rights being proposed. Moreover, the parallels to structures present in the political sphere may not be surprising to some, but as a person with a background in tech I was intensely curious as to why exactly this was the case.
I began to educate myself on the technology, methods, and standards involved in the SSI space and restarted work on the governance model I had put aside many months beforehand. I felt that in order to understand why similar structures had been produced independently based on certain principles, I should first consider the most basic facts regarding the nature of human interaction.
By investigating self-interest, centralization, and existing methods used for the decentralization of control, I have developed a conceptual governance model that may be of some use in digital identity and other systems of human interaction. This model can be used to examine existing systems of interaction and exchange and explain why some governance models are more successful than others. The model differentiates between centralization of function and centralization of control. This distinction can assist in understanding why systems are prone to corruption, what we can do to guard against this tendency, and how we can build governance structures that maintain and strengthen the collective interest over time. The structure proposed in the Three Concerns represents a repeatable design pattern that can be used to build the new governance models demanded by inherent user rights.
A Way Forward?
My continued work on CrossConnect has driven me to several conclusions. Specifically relating to telecommunications, Self-Sovereign Identity can be leveraged to construct a third mobile ecosystem, one which is free from the tyranny of proprietary identifiers. An open, interoperable, and neutral system of reachability can serve as a foundation on which to build future digital systems of interaction. A world may be constructed where 30% tariffs are a distant memory, but it will require a radically different design to what is currently taken for granted. Perhaps most challenging of all, it will require cooperation and a willingness to invest in the common interest.
More generally, our conception of self-interest in economic exchanges is fundamentally flawed and inadequate. We are biased towards centralization and have difficulty in separating the properties of function and control. As a result, we have made little progress in several thousand years of governance systems, repeatedly building the same types of structures throughout history. We lack the perspective required to innovate and iterate on our decentralized control structures which results in a historical absence of readily available governance frameworks that suit present day needs.
Work has only recently begun on models which resolve the conflicts of interest that inherent user rights produce. The concept of neutral constructs which represent the interest of users, such as MyData Operators, are only beginning to be understood as an important component of digital systems. We should recognize the present and historical difficulty of aligning humans towards the common interest for what it is, a woefully underdeveloped and poorly conceived understanding of the reality of our nature, resulting in the systems of human interaction and governance we have available to us today. Our technology has marched forward, but our minds are frozen in time.
What is required is a revolution of the foundations on which we build our systems and an inversion which creates a pull towards collective, as opposed to self, interest. If we wish to reach the full height of our potential, we must actively design our systems with our intellect, rather than allowing base animal instinct to guide and rationalize our decisions.
The Three Concerns governance model is an attempt to start from scratch, to begin anew. To construct a model for decentralized control structures based on the simplest biological truths. I do not wish to advance an ideology, or a political view. If I am to be found guilty for the crime of philosophy, then I confess to preferring existence over oblivion, and a desire to promote the common interest of all participants towards the correct operation of the system.
The Three Concerns may prove useful, or it may fail at being relevant or at providing any usable solutions. Its true importance lies in re-imagining the organization of the systems we construct. The tools that we build have come far, but we still possess the brains of our ancestors who roamed, foraged, and hunted in small groups across a vast and dangerous wilderness. The systems with which we organize ourselves are as primitive and unstable as the minds that constructed them and little has changed in how we conduct ourselves as a civilization.
Almost 2500 years ago, the ancient Athenian historian and general Thucydides wrote of the Peloponnesian War, saying “…the strong do what they can and the weak suffer what they must”. I would ask the reader if this assessment still rings true after more than two millennia of “progress”. We must continue the labour of building better systems to improve the present-day digital spaces we inhabit. If we can imagine what lays beyond the horizon of our experience, and chart a new course, ancient words may one day serve to remind us of our journey.